Welcome to our Pentest Files blog series.
Each blog post will present an interesting or dangerous finding one of our testers has identified in an actual recent pen-test, so you can see the kinds of cool things our pen-testers get up to, and also to help you take steps to prevent similar vulnerabilities in your own assets.
These findings are taken from real reports, anonymised, and published with kind permission from our clients.
Tester: Nabeel Ahmed
Company Revenue: $50m
Vertical: Health, Medical or Med-Tech
Impact: Complete application and user data compromise
What happened?
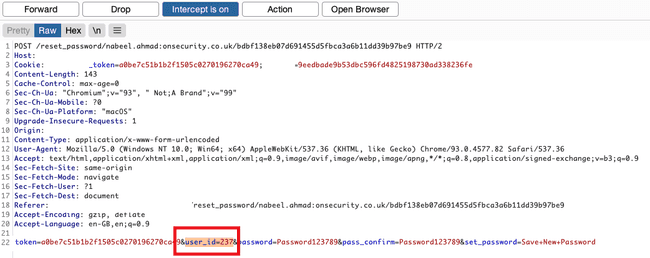
Nabeel took over the entire target application by exploiting a bug in the ‘forgotten password’ mechanism.
The Finding
An oldie but a goodie! Nabeel exploited what’s known as an Insecure Direct Object Reference (IDOR) vulnerability. Essentially, when the user chose a new password at the end of the password reset process, the ID of the user was sent with the password. By simply changing this user ID, Nabeel could reset the password of any application user, including the admin users.
The Fix
To prevent this, either:
- Determine the user whose password should be changed from the session information of the currently logged in user
- Ensure that the ID of the currently logged in user matches the ID supplied in the request
As well as this, all applications should adhere to the principle of never trusting any data that comes from the browser.




